-
Windows Security Settings: A Guide to Protecting Your System

Windows operating systems offer a comprehensive set of tools and settings to help safeguard users, devices, and data. Whether you’re managing a single personal computer or an enterprise network, understanding these security features is essential. This guide explores user roles, permission types, encryption options, and system protections that are built into Windows. Account Types: Local,…
-
Intro to Windows Event Viewer: What to Look For and Why

Whether you’re a system admin, help desk technician, or just a curious user, Windows Event Viewer is one of the most powerful tools built into the Windows operating system. It allows you to view detailed logs of system events, track down errors, and audit activities that happen behind the scenes. In this guide, we’ll walk…
-
How to Build a Home IT Lab on a Budget
Building a home IT lab is one of the most effective ways to gain practical experience in networking, system administration, and other areas. Whether you’re preparing for certifications like Cisco CCNA, CompTIA Network+, Microsoft 365 Fundamentals, or you’re trying to land that first IT help desk position, hands-on practice makes a huge difference. Fortunately, setting…
-
Understanding 802.11 Wi-Fi Standards: From 802.11a to Wi-Fi 6

Wi-Fi has become a staple of modern life, but behind the scenes, it’s built on evolving standards defined by the IEEE (Institute of Electrical and Electronics Engineers). These standards—often referred to by their 802.11 designations—determine the speed, range, and frequency of wireless networks. Here’s a breakdown of the major 802.11 standards and what they bring…
-
Common Wi-Fi Problems and How to Fix Them

The internet plays a vital role in our daily lives, serving as an essential tool for work, entertainment, and communication. However, Wi-Fi networks often face challenges such as slow connections or dropped signals, which can interfere with our online activities and ultimately impact our productivity. But what is Wi-Fi? Well Wi-Fi is a wireless technology…
-
Common Microsoft 365 Support Tickets and How to Resolve them
Microsoft 365 has become the productivity backbone for organizations of all sizes, offering a suite of powerful tools like Outlook, Teams, SharePoint, OneDrive, and more. But with widespread adoption comes a steady flow of support tickets. Whether you’re on an IT support team in an MSP or handling user issues solo as internal IT support,…
-
Essential Router Security and Configuration Tips for SOHO Networks
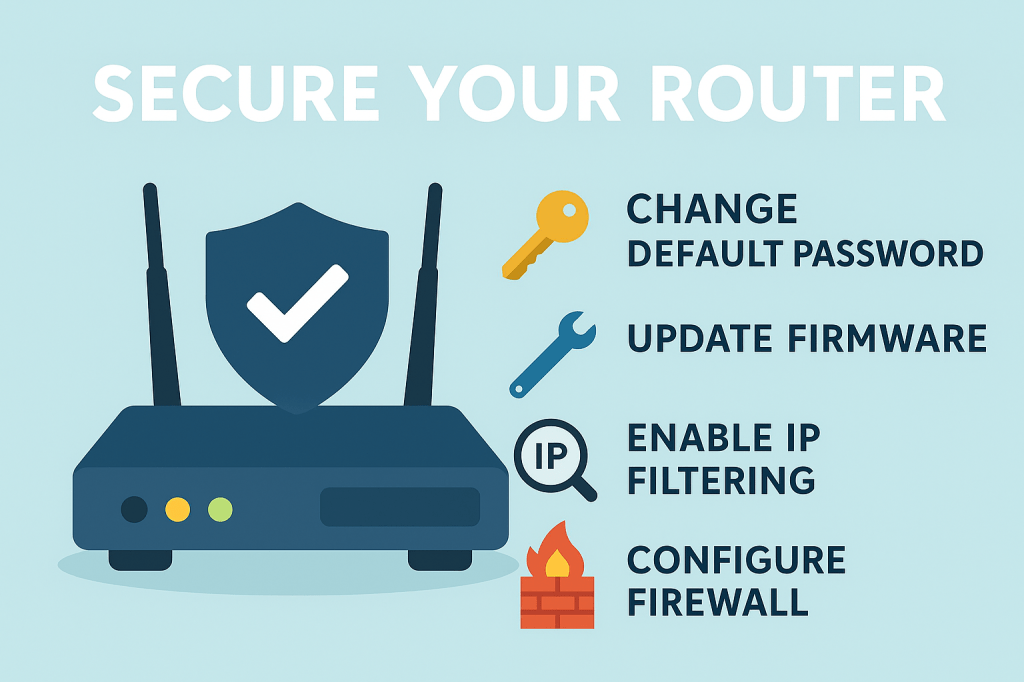
When setting up a new router—especially in a small office or home office (SOHO) environment—your first step should always be to change the default username and password. Default credentials grant full administrative access and are commonly known by attackers. Leaving them unchanged is like locking your front door but leaving the key under the welcome…
-
Understanding The OSI Model: The Network Layer (Layer 3)

Whether you’re studying for the CCNA, Network+, or just diving into network fundamentals, understanding how the network layer and IPv4 addressing work is essential. Layer 3 of the OSI model is where logical addressing and routing take place—and this blog post will help you understand how. What Happens at the Network Layer? The network layer…
-
Understanding Cisco Device Management and CLI Basics

In the world of enterprise networking, managing Cisco devices can be an essential skill—and it starts with understanding the operating systems Cisco uses and how to interact with their command-line interface (CLI). Cisco Operating Systems at a Glance Cisco devices don’t all run on the same operating system. Here’s a quick breakdown of the main…
-
Understanding Cross-Site Scripting (XSS): A Common Web Security Vulnerability

Cross-Site Scripting, commonly abbreviated as XSS, is one of the most prevalent security vulnerabilities found in web applications today. It exploits the trust users have in a website by injecting malicious scripts—usually written in JavaScript—into pages that other users view. In essence, XSS is malware that uses JavaScript to hijack user sessions, steal information, or…
-
Subscribe
Subscribed
Already have a WordPress.com account? Log in now.