Email is the backbone of communication for businesses and individuals alike—but it’s also one of the most common targets for cyberattacks. From phishing attempts to spoofed messages, attackers frequently try to trick individuals into believing an email is legitimate.
But how can we really tell if an email is from who it says it’s from?
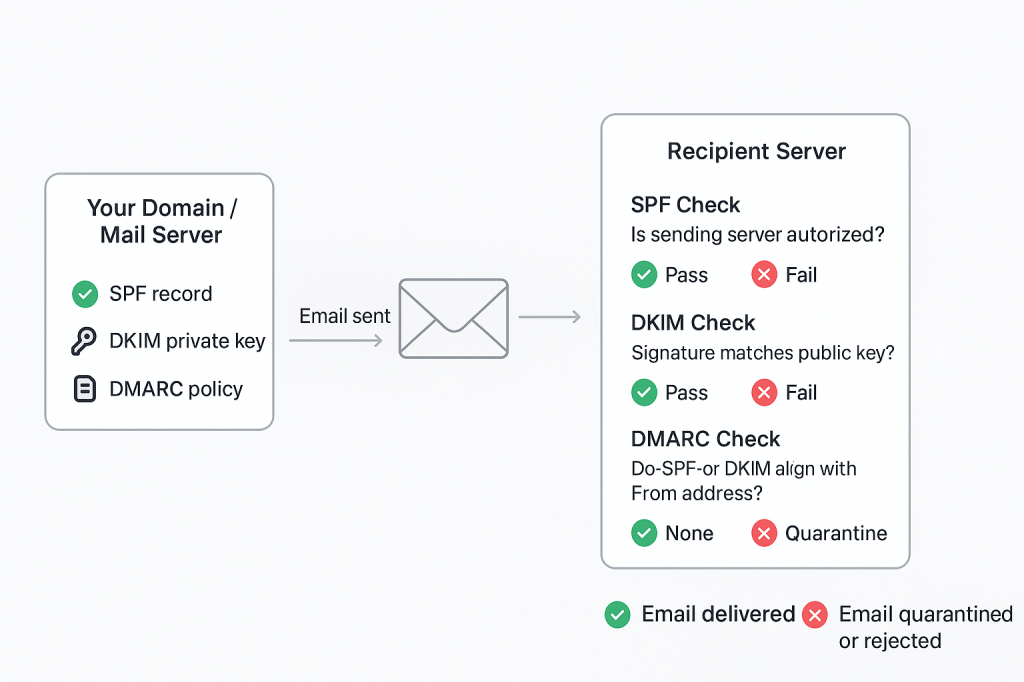
That’s where SPF, DKIM, and DMARC come in. These three technologies form the foundation of modern email authentication, helping to protect inboxes from fraud and ensuring trust in digital communication.
What Is SPF? (Sender Policy Framework)
SPF is like a guest list for mail servers. It allows the domain owner to specify which mail servers are authorized to send email on behalf of their domain.
- A domain owner publishes an SPF record in the Domain Name System (DNS).
- When an email is received, the recipient’s server checks the sender against that list.
- If the sending server isn’t on the list, the email fails SPF.
Example use case:
If your company uses both Microsoft 365 and Mailchimp to send emails, your SPF record should list both as authorized senders. If a spammer tries to send email pretending to be you from an unknown server, it won’t pass SPF.
What Is DKIM? (DomainKeys Identified Mail)
DKIM adds a layer of cryptographic verification. Instead of just checking where an email came from, it verifies that the contents of the email haven’t been tampered with in transit.
- The sending server “signs” the email with a private key.
- The receiving server checks that signature against a public key published in DNS.
- If the keys match, the email passes DKIM.
Why it matters:
Even if someone forges your “From” address, they won’t have access to your private signing key. That means their emails will fail DKIM validation.
What Is DMARC? (Domain-based Message Authentication, Reporting, and Conformance)
DMARC ties SPF and DKIM together and lets domain owners decide what should happen when an email fails authentication.
- A DMARC record in DNS tells receiving servers:
- Do nothing (monitor only).
- Quarantine suspicious messages.
- Reject them outright.
- It also enables reporting, so domain owners can see who is sending emails on their behalf.
Real-world example:
If PayPal publishes a strict DMARC policy, spoofed emails claiming to be from PayPal will fail SPF and DKIM checks and get blocked instead of landing in inboxes.
How They Work Together
- SPF checks: Is the sending server allowed?
- DKIM checks: Has the message been altered?
- DMARC checks: Do SPF and/or DKIM align with the “From” domain, and what should we do if they don’t?
When all three are in place, you get a much higher level of trust that an email truly came from the domain it claims to represent.
Why This Matters
Without these protections, it’s much easier for attackers to impersonate trusted brands and trick users into clicking malicious links, downloading malware, or giving up sensitive information. By enforcing SPF, DKIM, and DMARC, organizations not only protect their own reputation but also shield their customers and partners from fraud.
SPF, DKIM, and DMARC don’t guarantee that an email is 100% safe, but they form a powerful line of defense against phishing and spoofing. If you manage a domain, setting them up is one of the most impactful steps you can take to secure your email.
Leave a comment